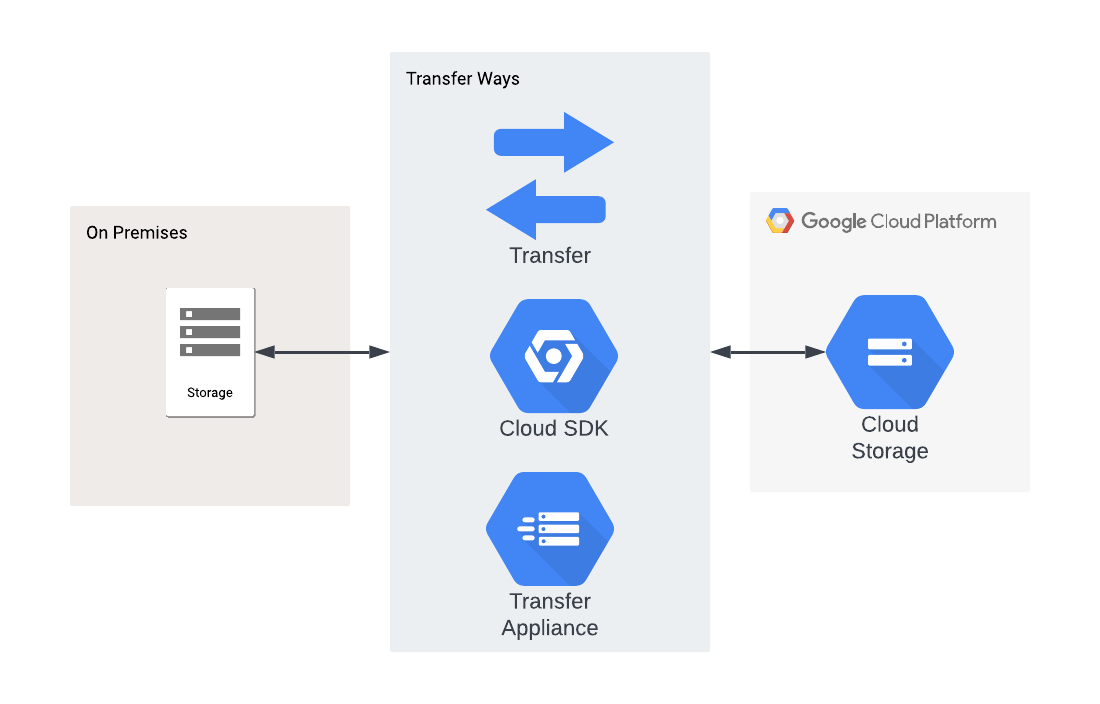
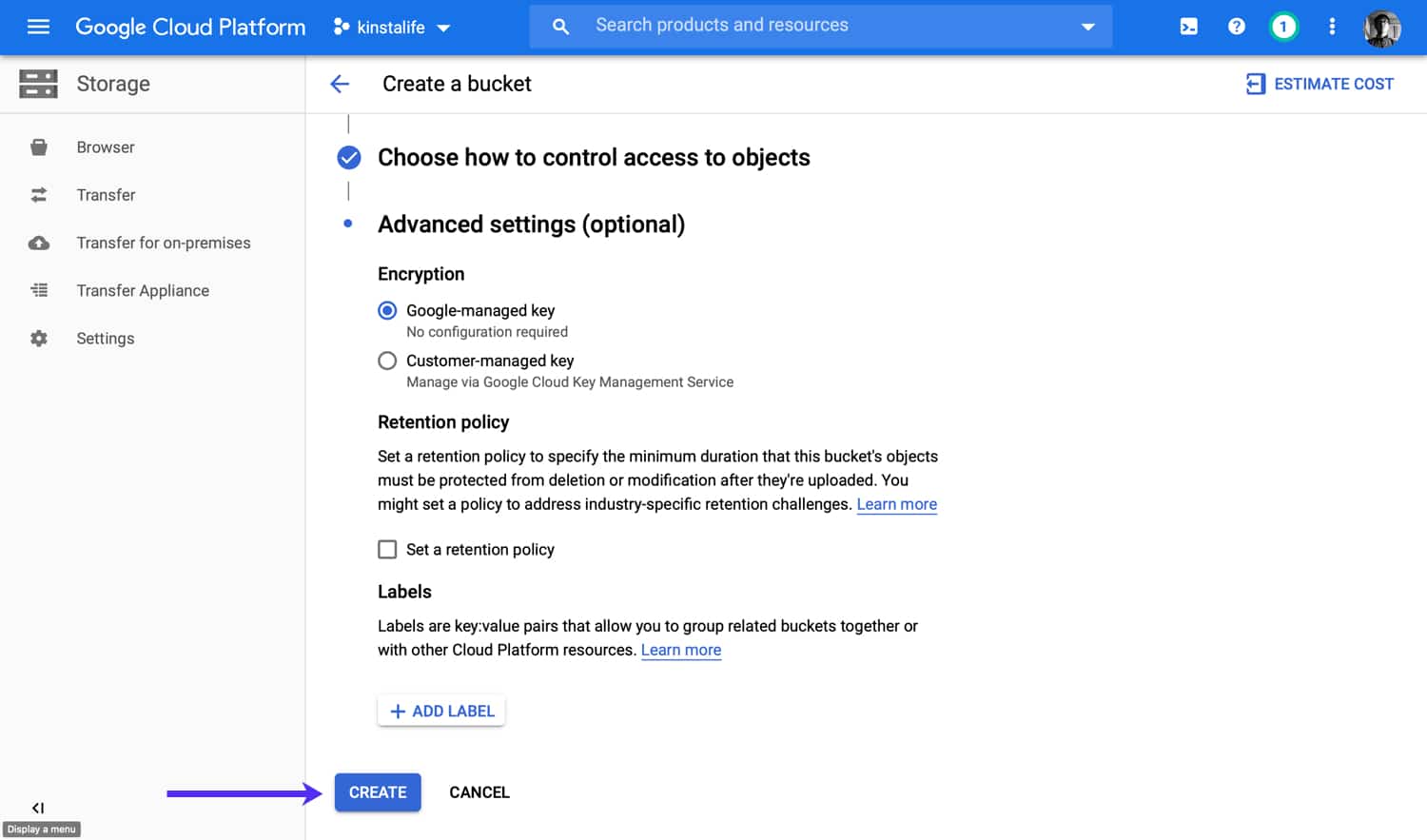
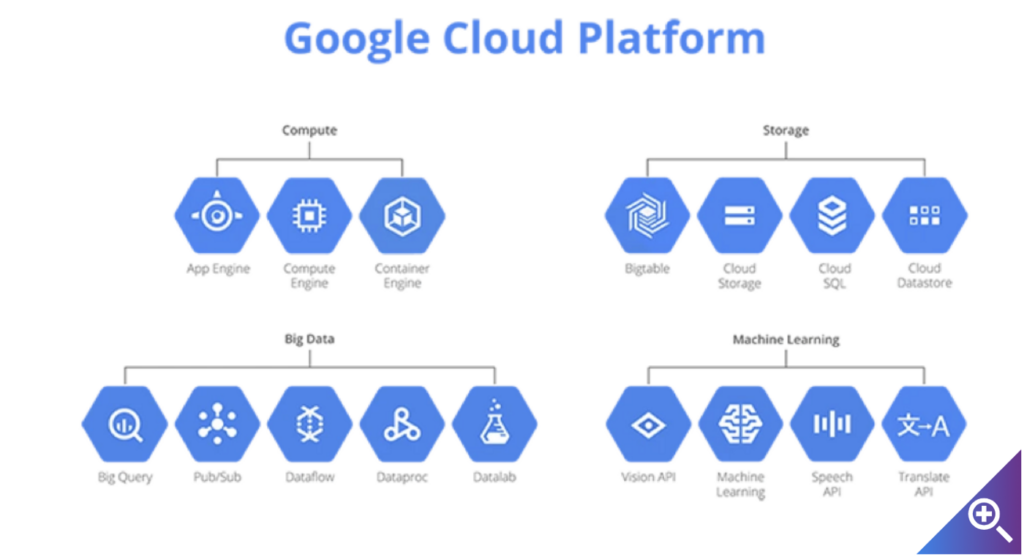
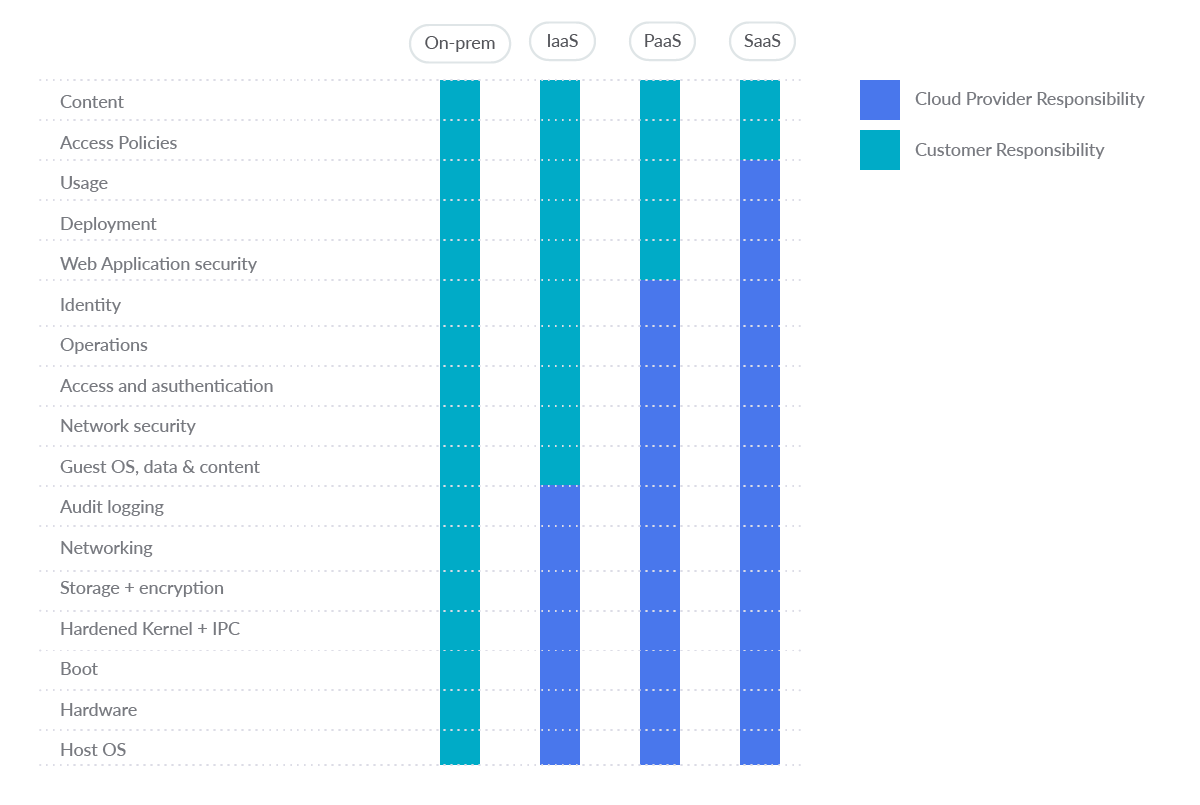
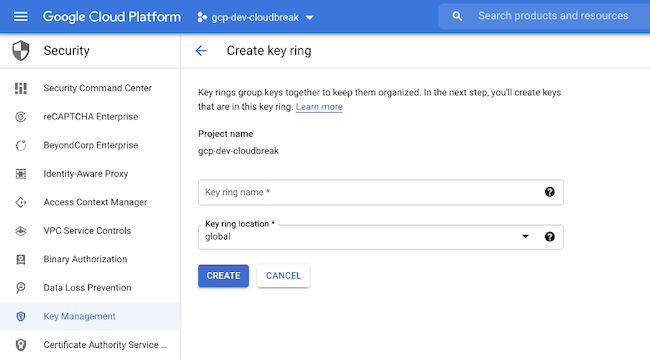
Understanding Customer-Managed Encryption Keys (CMEK) and Cloud KMS for Google Cloud Storage | by Selvi Perumal | Medium
GitHub - GoogleCloudPlatform/client-side-encryption: Client side encryption wrappers for gsutil and the GCS Python client library

Encrypting Stackdriver Logging sinks using Customer-Managed Encryption Keys for GCS | by Charles | Google Cloud - Community | Medium

Data Security in Google Cloud series — Part 1: Physical data encryption of sensitive data using Cloud DLP and KMS | by Daniel Villegas | Google Cloud - Community | Medium