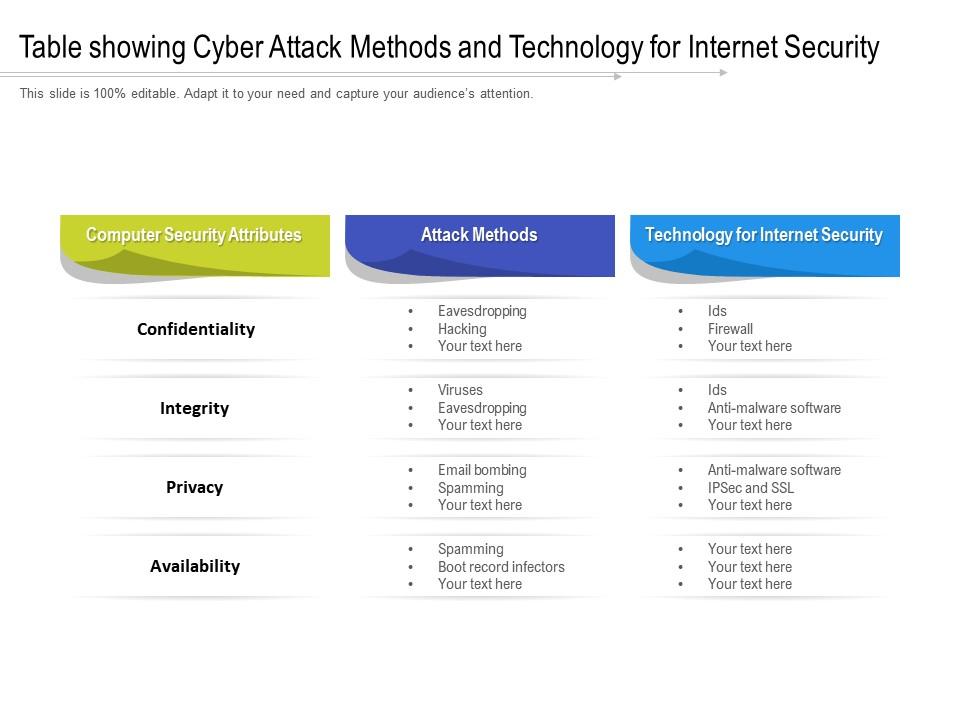
Table Showing Cyber Attack Methods And Technology For Internet Security | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

160 Security Guard Desk Stock Photos, Pictures & Royalty-Free Images - iStock | Security desk, Elevator, Cafeteria line






















